 打印本文
打印本文  关闭窗口
关闭窗口 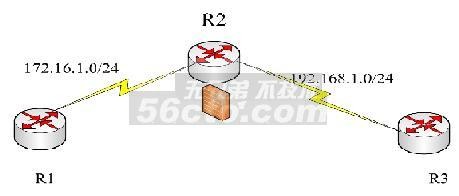
第一步:在R1 、 R2 、 R3上的预配置
r1(config)#int e0/0
r1(config-if)#ip add 172.16.1.1 255.255.255.0
r1(config-if)#no sh
r1(config)#ip route 0.0.0.0 0.0.0.0 172.16.1.2配置静态路由
r1(config)#^Z
r2(config)#int e0/0
r2(config-if)#ip add 172.16.1.2 255.255.255.0
r2(config-if)#no sh
r2(config-if)#int e2/0
r2(config-if)#ip add 192.168.1.2 255.255.255.0
r2(config-if)#no sh
r3(config)#int e2/0
r3(config-if)#ip add 192.168.1.3 255.255.255.0
r3(config-if)#no sh
r3(config)#ip route 0.0.0.0 0.0.0.0 192.168.1.2 配置静态路由
r3(config)#^Z
r3(config)#li vty 0 4
r3(config-line)#pass
r3(config-line)#password cisco
r3(config-line)#exit
| 热门推荐: | 打好基础的第一步 网吧布线全攻略 | 图解交换机与路由器组网技术 |
第二步:
在R2上配置zhang
r2#conf t
Enter configuration commands, one per line. End with CNTL/Z.
r2(config)#ip inspect name zhang tcp 检查TCP
r2(config)#ip inspect name zhang udp 检查udp
r2(config)#ip inspect udp idle-time 60 检查udp 的时间是60S
r2(config)#ip inspect name zhang icmp timeout 5 超时时间是5S
r2(config)#ip inspect name zhang http alert off 控制HTTP
r2(config)#
r2(config)#int e0/0
r2(config-if)#ip inspect zhang in 在e0/0接口检查流量是否满足以上所定义过的任何一条
r2(config-if)#exit
r2(config)#acce 100 deny ip any any log 做ACL拒绝IP的任何包通过
r2(config)#int e2/0
r2(config-if)#ip acce 100 in 将ACL要用到e2/0的进接口上
第三步: 从R1上TELNET R3
r1#telnet 192.168.1.3
Trying 192.168.1.3 ... Open
User Access Verification
Password:
r3>
从R3上TELNET R1
r3#telnet 172.16.1.1
Trying 172.16.1.1 ...
% Destination unreachable; gateway or host down
第四步:
从R1上ping R2直连接口
r1#ping 172.16.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 28/54/92 ms
从R2上ping R1直连接口
r2#ping 172.16.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 16/67/124 ms
从R2ping R3直连接口
r2#ping
*Mar 1 00:15:20.615: %SYS-5-CONFIG_I: Configured from console by console
r2#ping 192.168.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.3, timeout is 2 seconds:
*Mar 1 00:15:28.055: %SEC-6-IPACCESSLOGDP: list 100 denied icmp 192.168.1.3 -> 192.168.1.2 (0/0), 1 packet..... //说明icmp包可以到达,但 是没有回包
Success rate is 0 percent (0/5)
从R3ing R2连接口
| 热门推荐: | 打好基础的第一步 网吧布线全攻略 | 图解交换机与路由器组网技术 |
r3#ping 192.168.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.2, timeout is 2 seconds:
U.U.U //说明icmp包不可以到达目的地
Success rate is 0 percent (0/5)
r1#ping 192.168.1.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 76/124/156 ms
r2#debug ip inspect icmp
INSPECT ICMP Inspection debugging is on
r2#
*Mar 1 00:35:09.187: CBAC: ICMP Echo pkt 172.16.1.1 => 192.168.1.3
*Mar 1 00:35:09.187: CBAC: ICMP Echo pkt 172.16.1.1 => 192.168.1.3
*Mar 1 00:35:09.191: CBAC: ICMP Echo pkt 172.16.1.1 => 192.168.1.3
*Mar 1 00:35:09.263: CBAC: ICMP Echo Reply pkt 192.168.1.3 => 172.16.1.1
*Mar 1 00:35:09.375: CBAC: ICMP Echo pkt 172.16.1.1 => 192.168.1.3
*Mar 1 00:35:09.423: CBAC: ICMP Echo Reply pkt 192.168.1.3 => 172.16.1.1
*Mar 1 00:35:09.467: CBAC: ICMP Echo pkt 172.16.1.1 => 192.168.1.3
*Mar 1 00:35:09.531: CBAC: ICMP Echo Reply pkt 192.168.1.3 => 172.16.1.1
*Mar 1 00:35:09.563: CBAC: ICMP Echo pkt 172.16.1.1 => 192.168.1.3
r2#
*Mar 1 00:35:09.623: CBAC: ICMP Echo Reply pkt 192.168.1.3 => 172.16.1.1
*Mar 1 00:35:09.671: CBAC: ICMP Echo pkt 172.16.1.1 => 192.168.1.3
*Mar 1 00:35:09.735: CBAC: ICMP Echo Reply pkt 192.168.1.3 => 172.16.1.1
| 热门推荐: | 打好基础的第一步 网吧布线全攻略 | 图解交换机与路由器组网技术 |
【责任编辑 王凡】
 打印本文
打印本文  关闭窗口
关闭窗口